configure levels of access to web browser
EcoStruxure IT forum
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:58 PM . Last Modified: 2024-04-08 01:08 AM
configure levels of access to web browser
Is there a way or configuration that I can configure on the DCE V7.2.0 for prohibit an user or group of user from accessing to browser for launch to devices?
Objetive:
The customer would like configure an group of user that can access the devices by internal web browser of DCE, an another group of user that can't do it.
(CID:116365234)
- Labels:
-
Data Center Expert
Link copied. Please paste this link to share this article on your social media post.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:59 PM . Last Modified: 2024-04-08 01:07 AM
Hi Elivaldo da Silva Campos,
I also solved this problem and unfortunately the access control tools, built into the DCE server, did not help me.
My question is: is network access to monitoring devices from Private LAN carried out directly from clients PC or through a privateproxy embedded in the DCE server?
In the first case, I solved this problem by simply prohibiting network access by the external firewall to monitoring devices for users who should not have such access. But at the same time, they can monitor these devices without restrictions from the DCE WEB-console or from the DCE-client.
In the second case, I also used an external firewall, through which I allowed access to the DCE-server from Public LAN on port 80 (http) only to users, who must have via DCE privateproxy access to monitoring devices. And I allowed all other users on this external firewall to access the DCE server from Public LAN only on port 443 (https). On the DCE server, access to both the http (80) and https (443) protocols must be configured. This is in the first place. And secondly, on all monitoring devices from Private LAN it is necessary to configure access on port 80 (http). The https (443) protocol setting on the monitoring devices is possible, but not required. Thus, since access to monitoring devices from Private LAN is through the DCE privateproxy, which does not support working through the https protocol (this is its drawback, but for us this is an advantage 😀, we get an excellent access delimitation. Users, who do not need to have access to monitoring device interfaces have access to the DCE server only via the https protocol, but thus do not have access to the monitoring devices from either the DCE WEB-console or from the DCE client.
This is the solution I have been using successfully for several years.
With best regards.
(CID:116918078)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:58 PM . Last Modified: 2024-04-08 01:08 AM
Dear Elivaldo,
Struxureware Data Center Expert UI or Web browser access can be controlled by User and User Group authentication method. Therefore, please set the user password accordingly to provide an access to the UI and Web client of DCE.
There is a video tutorial available on Managing Users and User Groups on StruxureWare Data Center Expert.
Note: Device level access password also can be changed on the device web interface to prevent other users to access the device web interface.
I hope it helps.
Regards,
Bala
(CID:116917945)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:58 PM . Last Modified: 2024-04-08 01:08 AM
Hi team, good morning,
Thanks so much your help.
The devices are installed on private lan of DCE.
I can not prevent this access only selecting the role "StruxureWare Data Center Expert Proxy"?
I tryed to several test with this objetive, but I don't got success.
I am understanding that this role don't have function... is it?
Best regards, thank you so much again!!
(CID:116921107)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:58 PM . Last Modified: 2024-04-08 01:07 AM
That's why, what you want to do can not be done on the DCE-server in principle. Therefore, I published a practical workaround. And it is not the only one. For example, you can still restrict access based on the group policies of MS AD, if authentication is done in this way on the DCE-server. But this is a completely different topic...
I am always glad to help.
(CID:116921111)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:59 PM . Last Modified: 2024-04-08 01:07 AM
Hi Elivaldo da Silva Campos,
I also solved this problem and unfortunately the access control tools, built into the DCE server, did not help me.
My question is: is network access to monitoring devices from Private LAN carried out directly from clients PC or through a privateproxy embedded in the DCE server?
In the first case, I solved this problem by simply prohibiting network access by the external firewall to monitoring devices for users who should not have such access. But at the same time, they can monitor these devices without restrictions from the DCE WEB-console or from the DCE-client.
In the second case, I also used an external firewall, through which I allowed access to the DCE-server from Public LAN on port 80 (http) only to users, who must have via DCE privateproxy access to monitoring devices. And I allowed all other users on this external firewall to access the DCE server from Public LAN only on port 443 (https). On the DCE server, access to both the http (80) and https (443) protocols must be configured. This is in the first place. And secondly, on all monitoring devices from Private LAN it is necessary to configure access on port 80 (http). The https (443) protocol setting on the monitoring devices is possible, but not required. Thus, since access to monitoring devices from Private LAN is through the DCE privateproxy, which does not support working through the https protocol (this is its drawback, but for us this is an advantage 😀, we get an excellent access delimitation. Users, who do not need to have access to monitoring device interfaces have access to the DCE server only via the https protocol, but thus do not have access to the monitoring devices from either the DCE WEB-console or from the DCE client.
This is the solution I have been using successfully for several years.
With best regards.
(CID:116918078)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:59 PM . Last Modified: 2024-04-08 01:07 AM
Spezialist, good morning.
I understood that I can't prevent this access by DCE, but I need understand the funciton of "user roles" ==> "StruxureWare Data Center Expert Proxy", please, can you explained for me?
Certainly the customer will do this question for me.
Best regards
(CID:116921095)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:59 PM . Last Modified: 2024-04-08 01:07 AM
Hi Elivaldo da Silva Campos,
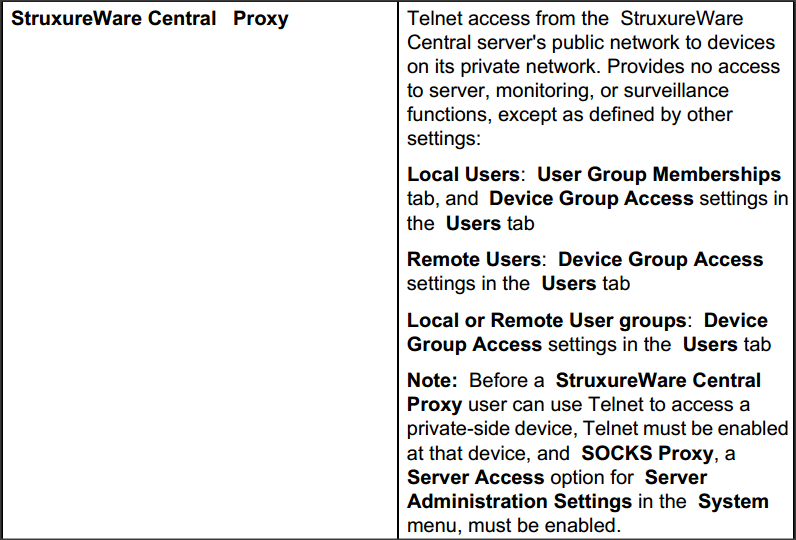
It seems, that the DCE online help is somewhat outdated: I still could not understand, here is the Telnet access and what does it have to do with the SOCKS proxy? This is a question, primarily for DCE developers.
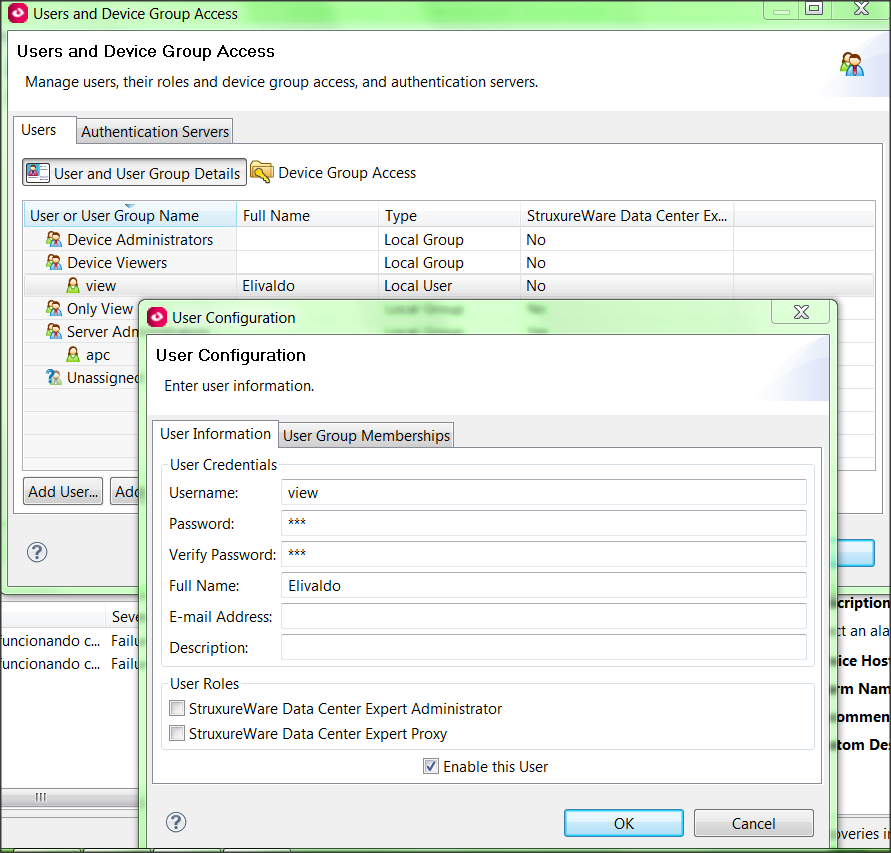
And now, in fact: the StruxureWare Central Proxy role is used, if you want to allow launch to the locally installed APC Adwanced View software from the DCE-client (and only). For example:
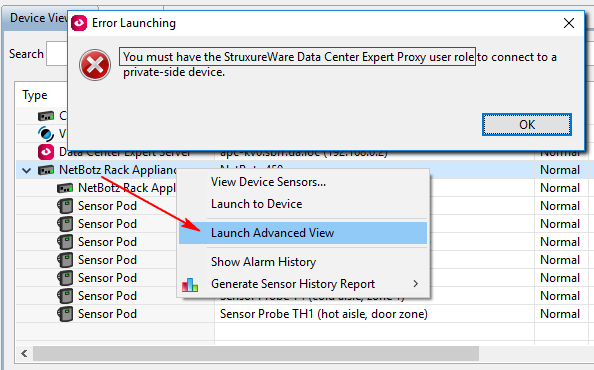
And this, in turn, gives access to the 80 (http) port (Telnet by default is disabled) of the NetBotz appliance (and only) in Private LAN via the built-in DCE-server SOCKS proxy (if it is of course enabled) through port 1080. For example:
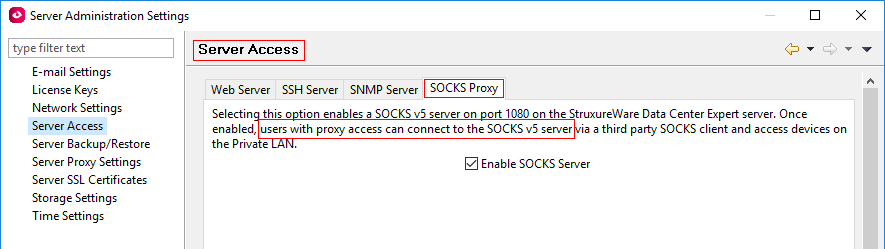
I.e., if you sum up, the role StruxureWare Central Proxy allows you to access the NetBotz appliance (and only) in Private LAN and only from the DCE-client.
With best regards.
(CID:116921101)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:59 PM . Last Modified: 2024-04-08 01:07 AM
spezialist, good morning,
Thank you so much, I appreciate your answer.
Best regards,
(CID:116921099)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 02:59 PM . Last Modified: 2023-10-22 04:27 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.
