Ask our Experts
Didn't find what you are looking for? Ask our experts!
Share Your Feedback – Help Us Improve Search on Community! Please take a few minutes to participate in our Search Feedback Survey. Your insights will help us deliver the results you need faster and more accurately. Click here to take the survey
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
Search in
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:15 PM . Last Modified: 2024-04-03 02:43 AM
Our customer has Netbotz 200 at a remote datacenter connected to DCE at main datacenter over corporate network . After their IT security audit it was raised the the Netbotz 200 has open ftp ports and the password is week. The netbotz is connected to Data Center Expert. How best can we guarantee the security of the APC equipment and DCE on the network.
They are concerned about preventing from malicious code upload or from other people who are ware of the password from accessing the netbotz via ftp (or other protocols over the corporate network) and make harmful changes. Is netbotz ftp read-only, or is there a way to make it read only without affecting the connection with DCE.
Can I have a separate user for connecting to DCE and onother for http or https.
What are the best IT security measures we can implement for all APC and Schneider Electric (UPSes, Inrows, PDUs etc) as they support network critical systems
I saw these commands are available in ftp
rename, delete, mdelete
(CID:143757615)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:15 PM . Last Modified: 2024-04-03 02:43 AM
Hi Cleopas,
If your customer feels that their password is weak, they should change their password. The FTP password is the admin password on those NetBotz 200 devices. If they do not like FTP, they can also disable FTP and use SCP.
The same passwords for administrators can also be used for ftp, you can't change that. My suggestion would be to limit access to the NetBotz appliance , UPS, etc by only allowing them read only access.
Thanks,
Steve
(CID:143757660)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:15 PM . Last Modified: 2024-04-03 02:43 AM
How do make the units read-only, I would like to maintain a connection with the DCE at main datacenter.
Can admin make harmful changes like delete using FTP?
Is FTP required by DCE? If not I may need to disable it.
(CID:143757926)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:15 PM . Last Modified: 2024-04-03 02:43 AM
Hi Cleopas,
When you discover a device, DCE needs FTP (or scp) to pull an alert definition file from the device. When configuring a device through DCE, the same protocol(s) are used to pull / push the configuration file. Finally, the same protocol is used to push a firmware upgrade. These must be enabled (either FTP or SCP) for full compatibility with DCE.
What are you worried about deleting? You can't delete the firmware but you can delete the event log for instance. This would be similar access as if you had admin access to the web page.
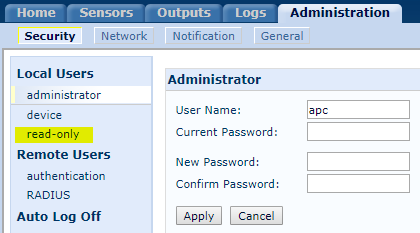
For security purposes, you can configure 3 levels of users on the device itself. Here's the old firmware on a NetBotz 200:
Here's what it looks like on the newer cards:
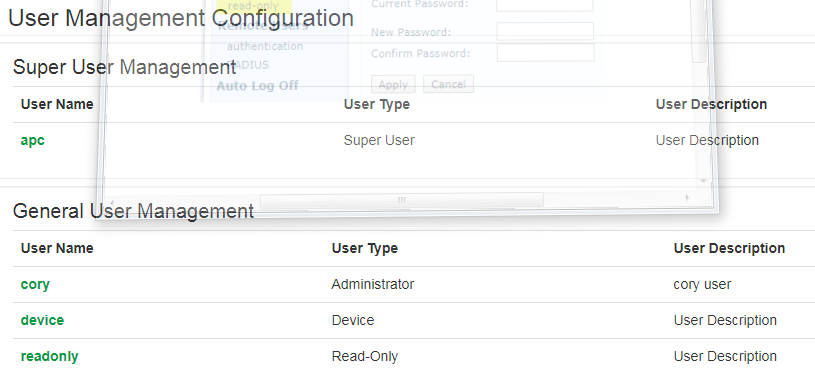
If you do not want someone to have the user name and password to be allowed to FTP to the card directly, provide them with the read only user name and password.
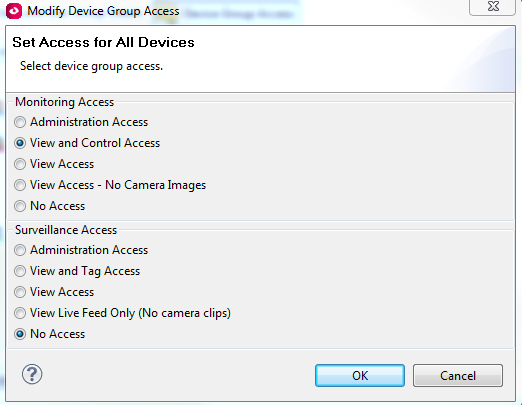
If you're using DCE, You can also give people granular access to device groups:
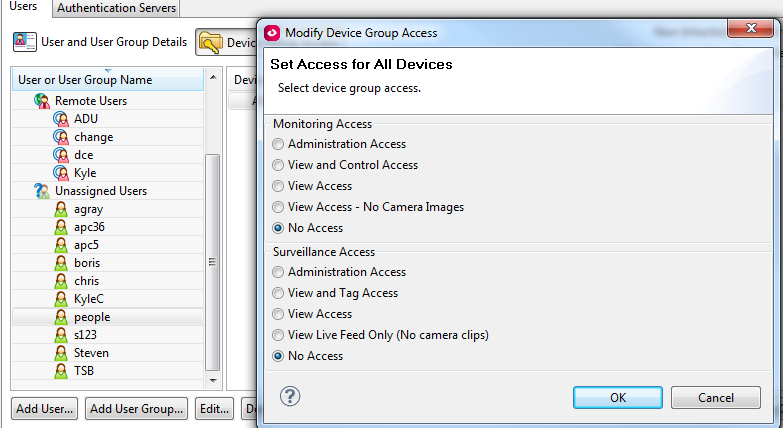
You can specify device launch settings for each device so that when they double click a device in DCE, they only get the type of access provided by the user name and password used:
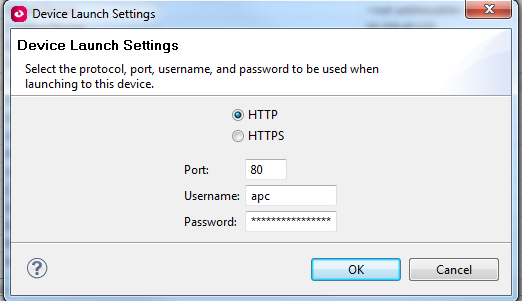
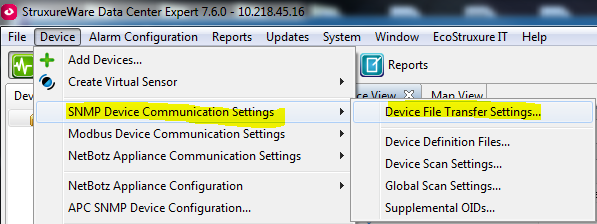
If you do not have the proper access to DCE, you will also not have access to see the device file transfer settings which is where the FTP or SCP settings are held for the purposes that I mentioned in the beginning:
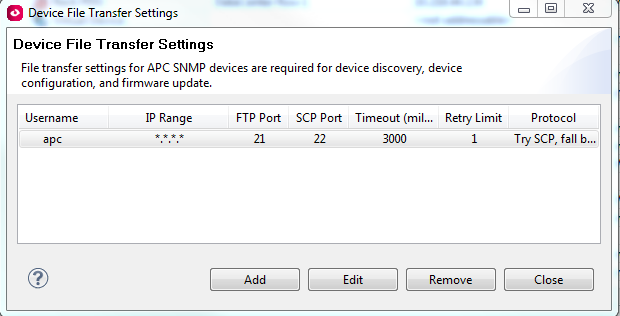
So an admin will be able to see these settings:
so if I were to give you view and control access over devices:
You wouldn't even have the "device" menu required to access these user names and passwords:
Steve
(CID:143758723)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:15 PM . Last Modified: 2023-10-22 02:40 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
You’ve reached the end of your document
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.