Ask our Experts
Didn't find what you are looking for? Ask our experts!
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
Search in
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:00 AM . Last Modified: 2024-04-05 03:08 AM
I have a customer that is receiving a cascade of alerts when his monitor servers ping his network management card.
I know he can disable this alert but then he won't be able to receive notification in the event of a genuine malicious attack.
Is there any way to put is server on a white list to prevent these nuisance e-mails.
(CID:128065151)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2024-04-05 03:08 AM
Dear Adrian Carroll,
As Steven Marchetti correctly answered, a similar question :
Your first best bet would be to stop the scanning with incorrect credentials...
I.e., in your case, your 3-rd party monitoring server should poll the NMC by the SNMP protocol with the correct community strings (see the settings inside the NMC in the SNMP section).
I hope this is what you need.
With respect.
(CID:128065174)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2024-04-05 03:08 AM
Dear Adrian Carroll,
As Steven Marchetti correctly answered, a similar question :
Your first best bet would be to stop the scanning with incorrect credentials...
I.e., in your case, your 3-rd party monitoring server should poll the NMC by the SNMP protocol with the correct community strings (see the settings inside the NMC in the SNMP section).
I hope this is what you need.
With respect.
(CID:128065174)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2024-04-05 03:08 AM
Hi ,
The path given by Steven is the path from the DCE. Is there a way to find out the correct community strings from the NMC itself?
(CID:128065951)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2024-04-05 03:07 AM
Dear Adrian Carroll,
...Is there a way to find out the correct community strings from the NMC itself?
Yes, of course.
I explain for SNMPv1: in order for NMC not to flood you with e-mail messages about unauthorized SNMP access attempts, you need to specify the correct Read-only Community Name on your 3-rd party monitoring server for your NMC (please, contact the administrators of this 3-rd party monitoring server).
For example, you need login to the web-GUI of your NMC along the path as in my screenshot (for SNMPv1):
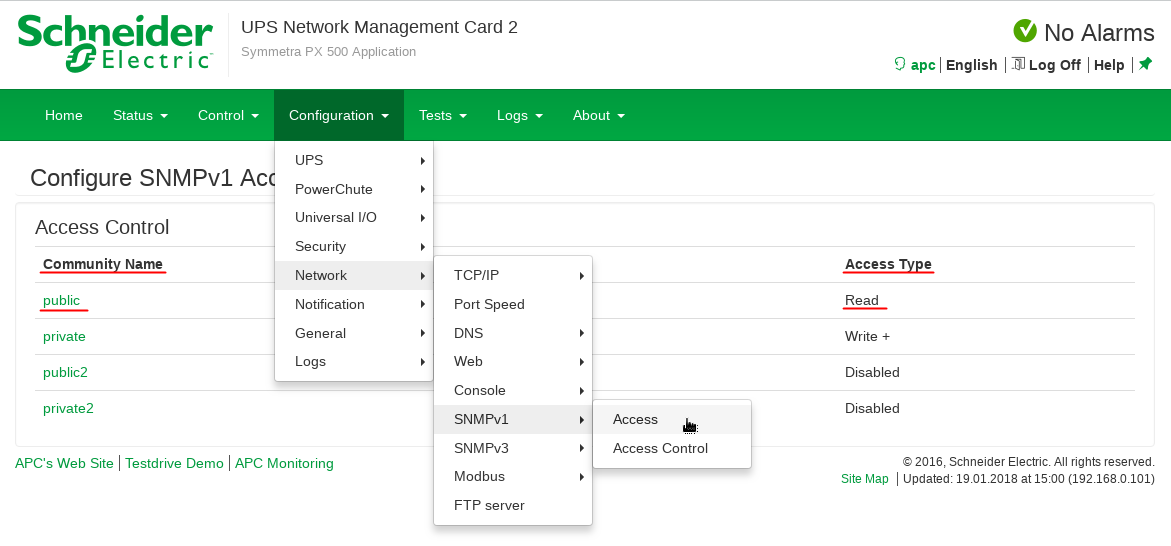
And then we'll see, that for this NMC Read-only Community Name = public (this is the default value, I did not change it, although I could do it). Now, this value, i.e. public must be specified on the 3-rd party monitoring server to poll this your NMC.
If on your 3-rd party monitoring server to poll this NMC is specified the incorrect value of Read-only Community Name, it causes a lot of e-mail messages from the NMC about unauthorized SNMP access attempts.
I hope I understood you correctly and it will help you.
If there are more questions, please ask.
(CID:128065948)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2024-04-05 03:07 AM
That's great. Thank you very much for your assistance.
(CID:128065943)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2024-04-05 03:07 AM
Ok, thanks for the feedback 😀.
(CID:128065938)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 04:01 AM . Last Modified: 2023-10-22 01:52 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
You’ve reached the end of your document
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.