Ask Me About Webinar: Data Center Assets - Modeling, Cooling, and CFD Simulation
Join our 30-minute expert session on July 10, 2025 (9:00 AM & 5:00 PM CET), to explore Digital Twins, cooling simulations, and IT infrastructure modeling. Learn how to boost resiliency and plan power capacity effectively. Register now to secure your spot!
DCO vulnerabilities SERVER: MiniServ/1.820
EcoStruxure IT forum
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:28 PM . Last Modified: 2024-04-03 11:54 PM
DCO vulnerabilities SERVER: MiniServ/1.820
Hi Support,
We require your assistance with this matter.
Preview:
- one of the biggest national banks in our country has the DCO running in a virtual server
- Our customer used a third party utility to detect vulnerabilities. They use “QRadar”
- The DCO is running in version 8.0.3
Vulnerabilities:
The customer is using the QRadar utility and they want to solve the vulnerability below:
CVE ID: 2017-15645,2007-5066
Vulnerability ID: Webmin create_job.cgi cross-site request forgery
Vulnerability Description: SERVER: MiniServ/1.820
Port: 10000
Concern: This application is prone to this vulnerability because of an unknown reason, allowing an attacker to execute arbitrary commands and escalate privileges.
Solution: No remedy available as of October 16, 2017.
(CID:136645387)
- Labels:
-
Data Center Operation
- Tags:
- bug
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:28 PM . Last Modified: 2024-04-03 11:54 PM
Hello Andres.
The above DCO release you mention is quite old. Current DCO release is 8.2.12. Each of the DCO releases since the mentioned 8.0.3 release include patches/updates to address security and vulnerabilities. We scan/verify known vulnerabilities against each new release before it becomes available to the public.
We would recommend you consider upgrading your DCO 8.0.3 installation to a more current release.
Regards
Greg Sterling
(CID:137104964)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:28 PM . Last Modified: 2024-04-03 11:54 PM
Hi Greg,
We upgraded the DCO software as you requested, but the vulnerability persist.
CVE ID: 2017-15645,2007-5066
Vulnerability ID: Webmin unspecified URL command execution
Vulnerability Description: SERVER: MiniServ/1.820
Port: 10000
Concern: This application is prone to this vulnerability because of an unknown reason, allowing an attacker to execute arbitrary commands and escalate privileges.
Solution: Upgrade to the latest version of Webmin (1.370 or later), available from the Webmin Web site: Security Alerts. See References.
Please help!!
(CID:140711698)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:28 PM . Last Modified: 2024-04-03 11:54 PM
We'll ask development to comment further, but when I look at these CVE definitions (CVE ID: 2017-15645,2007-5066) they state these vulnerabilities are addressed by webmin versions 1850 and 1370 respectively.
If you upgraded to DCO 8.2.12 then your webmin version should be 1890. If you logon to your webmin gui (https://dco-server-ip:10000/) the webmin version should be visible on the system information page when you login.
Regards
Greg Sterling
(CID:137729396)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:29 PM . Last Modified: 2024-04-03 11:54 PM
Hi Greg,
We performed the webmin upgrade as you mentioned.
The webmin works in version 1.900
But now we have more vulnerabilities.
Please check the attached image.
We need to purge this list.
We appreciate all your help.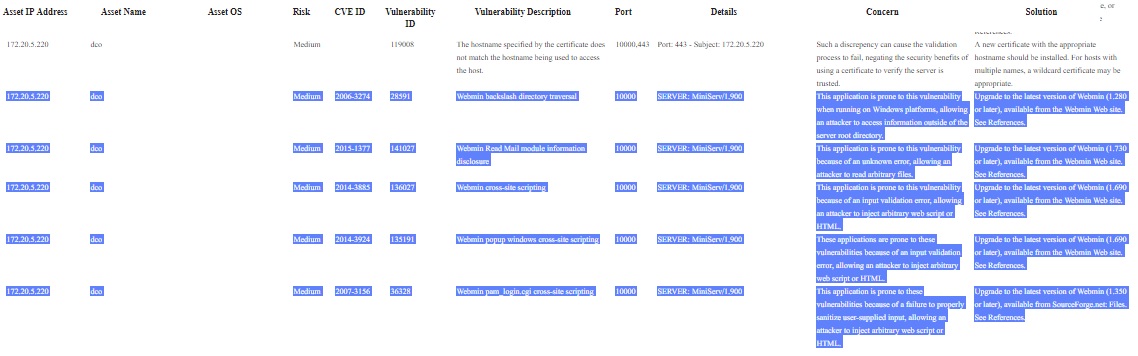
(CID:138381699)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:29 PM . Last Modified: 2024-04-03 11:54 PM
Hello Andres
Did you update webmin only or both DCO and webmin?
Regards
Greg Sterling
(CID:138381738)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:29 PM . Last Modified: 2024-04-03 11:53 PM
Hello Greg,
Both at the same time.
The resolution instructions for many of the vulnerabilities are to upgrate the webmin versión to a newest versión. (Please check atached file = Vulnerabilidades DCO.xlsx)
The webmin is aleady in versión 1900.
Could this be managed as a false -positive?
Vulnerabilidades DCO.xlsx
(CID:140217735)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:29 PM . Last Modified: 2024-04-03 11:53 PM
Hello Andres. I have asked our dev team to comment on your recent response.
Regards
Greg Sterling
(CID:140218061)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:29 PM . Last Modified: 2024-04-03 11:53 PM
Hello Greg,
Any update?
(CID:140711587)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 02:29 PM . Last Modified: 2023-10-22 01:46 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.
Welcome!
Welcome to your new personalized space.
of
