Issue
After configuring SSL certificates manually, having an incompatible Host Certificate and Key file can cause the import to EBO to fail.
Product Line
EcoStruxure Building Operation
Environment
- Building Operation Enterprise Central
- Building Operation Enterprise Server
- Building Operation Automation Server
Cause
Host Certificate provides the public key for which the private key is paired. An unmatched Host Certificate and private key will cause the certificate import to fail.
Resolution
While managing certificates manually, it is recommended to check that the Host Certificate and Key files are a matching pair.
- Using the provided Host Certificate (.pem) file and private key (.key or .prv) file
- Download OpenSSL v1.1.1 Light choosing the EXE file type and correct version (Win64 or Win32), as the latest version letter will be posted to Win32/Win64 OpenSSL Installer for Windows - Shining Light Productions (slproweb.com) or OpenSSL installed with EBO
- If using Shining Light installer, it is recommended to open command prompt from where certificates are stored on the desktop and substitute openssl with "C:\Program Files\OpenSSL-Win64\bin\openssl.exe". Working with certificate files on the Windows desktop ensures the user will have the correct permission to run the commands, unlike putting certificate files in the Program Files directory where openssl.exe resides.
- Open PowerShell or Command Prompt
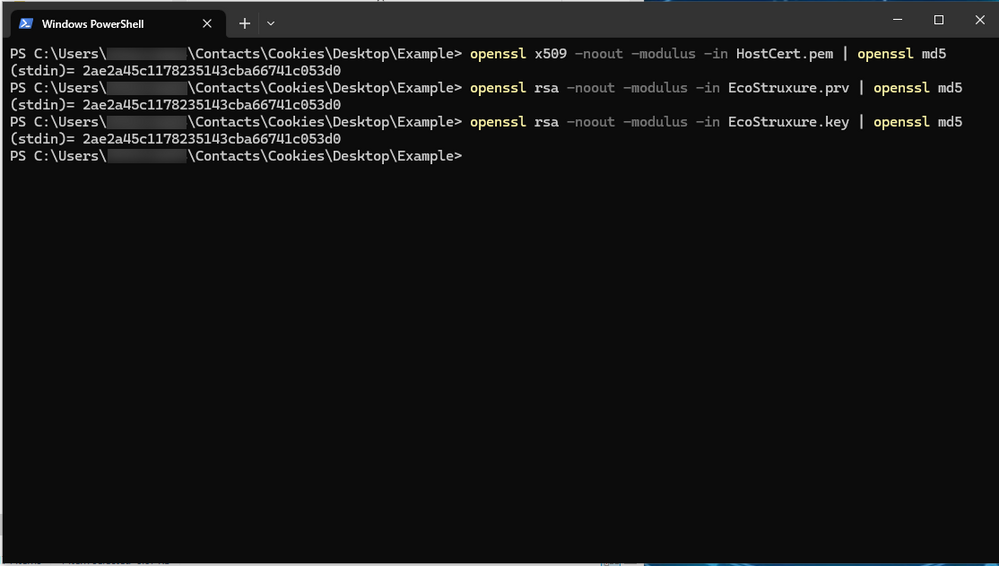
- Obtain the host certificate md5 hash with this command:
- openssl x509 -noout -modulus -in filename.pem | openssl md5
- Obtain the private key md5 hash using the command below. Use the correct command based on the key file file type
- openssl rsa -noout -modulus -in filename.prv | openssl md5
- openssl rsa -noout -modulus -in filename.key | openssl md5
In this example, the Host Certificate is HostCert.pem and the private key is EcoStruxure.key. The private key was converted to EcoStructure.prv using Step 12 of Installing an SSL Certificate from an External CA - Communities (se.com)
These commands make the hash more readable to human eye. We use openssl to inspect the x509 for Certificate and encryption type rsa for the key to produce the modulus (-modulus), which is a long string. You then use (-noout) to prevent the full modulus from printing to the screen. You then create a shorter md5 hash so the human eye can easily compare them. If the md5 hashes match, that indicates that the modulus is a match and proves that the certificate/key is a pair.