Issue
Does the Automation Server support network authentication via Radius Server (IEEE 802.1X)?
Product Line
EcoStruxure Building Operation
Environment
Building Operation Automation Server
Cause
AS supports network authentication via Radius Server (IEEE 802.1X)?
Resolution
RADIUS and IEEE 802.1X are not the same thing, although they can be used together.
Remote Authentication Dial In User Service (RADIUS) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for computers to connect and use a network service. RADIUS is a client/server protocol that runs in the application layer, using UDP as transport.
The RADIUS server is usually a background process running on a UNIX or Microsoft Windows server.
RADIUS serves three functions:
- to authenticate users or devices before granting them access to a network,
- to authorize those users or devices for certain network services and
- to account for usage of those services.
IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN. It is a mechanism used in (mostly) switches and wireless access-points to allow or block devices to access the network (or granularly allow access to parts of it).
For example, if you have a network port in a meeting room, you can enable 802.1x on the switch port and configure it in such a way that when an employee connects they have access to the entire network, but if a guest connects (with a temporary password) they can only reach the Internet and if a passer-by is tempted to try his luck, they cannot access anything at all.
Does IEEE 802.1X also use RADIUS as it's underlying authentication mechanism?
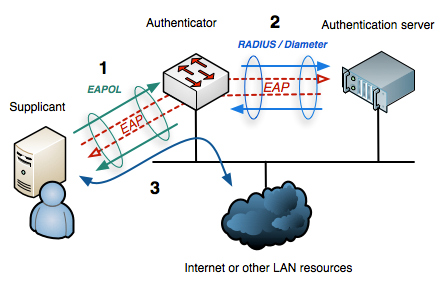
Yes and no. IEEE 802.1x uses Extensible Authentication Protocol (EAP), the drawing below shows that for wired 802.1x:
- EAP over LAN (EAPoL) is used between the Supplicant (software on a computer) and the Authenticator (switch).
- EAP is then usually tunneled over Radius between the Authenticator and the Authentication Server, but it can also be done over Diameter (the successor to Radius).
For wireless, it is similar in the sense that there is also no Radius between the supplicant and the authenticator, only between the authenticator and the Authentication Server (to tunnel the EAP).
From EBO 2022 the AS-P and AS-B can be configured as supplicants on a network protected by IEEE 802.1X security. See the IEEE 802.1X Security Webhelp topic for further details.
Note: MPx/RPx do not support 802.1x network authentication, see the SpaceLogic controllers MPx/RPx do not support 802.1x network authentication Knowledge Base article for further details.