We Value Your Feedback!
Could you please spare a few minutes to share your thoughts on Cloud Connected vs On-Premise Services. Your feedback can help us shape the future of services.
Learn more about the survey or Click here to Launch the survey
Schneider Electric Services Innovation Team!
Vulnerability found in DCE & DCO
EcoStruxure IT forum
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:47 PM . Last Modified: 2024-04-04 02:46 AM
Vulnerability found in DCE & DCO
Hi Team,
Customer ran a vulnerability scan on his network and did find the following on DCE & DCO, it all has to do with a update of OpenSSH to a version 7.7p1 or later.
DCE = 7.5 & DCO = 8.2.2
In which version of DCE/DCO will this be updated ?
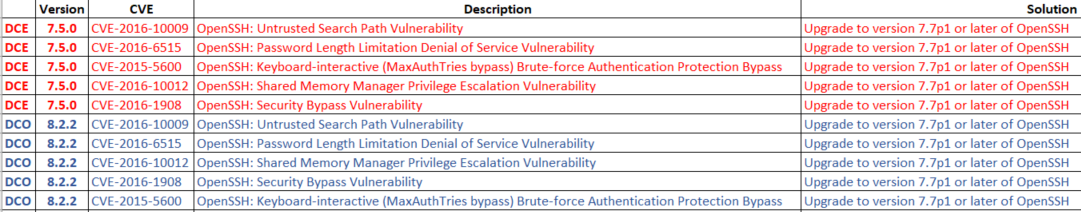
(CID:134026904)
Link copied. Please paste this link to share this article on your social media post.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:47 PM . Last Modified: 2024-04-04 02:46 AM
Hi Cees,
. The current suggestion I can make and what we’re asked to do for customer is to note:
- For customers or researchers to report incidents, Schneider provides the external email address, cybersecurity@schneider-electric.com
- All vulnerability disclosures are reported on Schneider Electric's global web site; SE.com Cybersecurity Portal. You can review Security Notifications here as well
And that
- Schneider Agents should refer customer to cybersecurity@schneider-electric.com or https://www.schneider-electric.com/en/work/support/cybersecurity/report-an-incident.jsp to submit their question or concern along with any pertinent details.
- Customers should expect a response within 3-5 business days.
Thanks,
Steve
(CID:134027416)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:47 PM . Last Modified: 2024-04-04 02:46 AM
...Very interesting, but even the most recent official updates for RHEL-7.5 (and for CentOS-7.5) offer a vulnerable version of OpenSSH:
$ uname -a
Linux 3.10.0-862.11.6.el7.x86_64 #1 SMP Fri Aug 10 16:55:11 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
$ rpm -qa | grep ssh
openssh-server-7.4p1-16.el7.x86_64
openssh-7.4p1-16.el7.x86_64
openssh-clients-7.4p1-16.el7.x86_64
libssh2-1.4.3-10.el7_2.1.x86_64
(CID:134027175)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:47 PM . Last Modified: 2024-04-04 02:46 AM
hmm, interesting ...
(CID:134027218)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:47 PM . Last Modified: 2024-04-04 02:46 AM
Hi Cees,
. The current suggestion I can make and what we’re asked to do for customer is to note:
- For customers or researchers to report incidents, Schneider provides the external email address, cybersecurity@schneider-electric.com
- All vulnerability disclosures are reported on Schneider Electric's global web site; SE.com Cybersecurity Portal. You can review Security Notifications here as well
And that
- Schneider Agents should refer customer to cybersecurity@schneider-electric.com or https://www.schneider-electric.com/en/work/support/cybersecurity/report-an-incident.jsp to submit their question or concern along with any pertinent details.
- Customers should expect a response within 3-5 business days.
Thanks,
Steve
(CID:134027416)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:47 PM . Last Modified: 2024-04-04 02:46 AM
Thanks Steve, I will contact the customer to sent their vulnerability report to the email address mentioned above.
Regards,
Cees
(CID:134027427)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:48 PM . Last Modified: 2024-04-04 02:46 AM
Hi Cees,
Here is a brief summary of our responses to the vulnerabilities highlighted within the underlying packages installed on DCE 7.5. A follow on post will do the same for DCO.
CVE-2016-1908 and CVE-2015-5600 are both addressed within DCE 7.5 as it uses a newer version of openssh (openssh-5.3p1-123.el6_9.x86_64), which contains fixes for both.
The other 3 issues are not technically fixed in our shipping version of openssh, as fixes are not available on CentOS 6, but they are generally not exploitable and/or can be mitigated by a user. Details below on that below:
- CVE-2016-10009
- Statement from RedHat:
In order to exploit this flaw, the attacker needs to have control of the forwarded agent-socket and the ability to write to the filesystem of the host running ssh-agent. - Users are not provided with the DCE root password, and cannot access the filesystem to leverage the issue, unless under the direction of technical support.
- Statement from RedHat:
- CVE-2016-6515
- SSH is disabled by default on DCE 7.x, and normally not needed unless technical support needs to access the DCE server.
- If concerned about this issue, leave SSH turned off, unless required for technical support usage.
- CVE-2016-10012
- Statement from RedHat:
In order to exploit this flaw, the attacker needs to first compromise the sandboxed privilege-separation process by using another security flaw. Because of this restriction for successful exploitation, this issue has been rated as having Low security impact. - SSH is disabled by default on DCE 7.x, and normally not needed unless technical support needs to access the DCE server.
- If concerned about this issue, leave SSH turned off, unless required for technical support usage.
- Statement from RedHat:
It's worth noting that fixes are available for these issues within CentOS 7. DCE will move to this version in a future release, likely within 2019.
Please let me know if you or your customer have any follow on questions or concerns and we'd be happy to answer them.
Thanks,
Brian Behbehani
(CID:134028283)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:48 PM . Last Modified: 2024-04-04 02:46 AM
Hi Brian,
Thanks a lot for your clear answer, will sent this info to the customer.
Will wait for the response on DCO,
Best regards,
Cees
(CID:134028503)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:48 PM . Last Modified: 2024-04-04 02:46 AM
Hi Cees
As Brian Behbehani mentioned fixes are available for these issues within CentOS 7, Data Center Operations 8.2.2 is shipped with CentOS 7.4 and openssh packages that are installed contain fixes for mentioned vulnerabilities.
OpenSSH packages that are installed with Data Center Operations 8.2.2 are
openssh-server-7.4p1-13.el7_4.x86_64
openssh-7.4p1-13.el7_4.x86_64
openssh-clients-7.4p1-13.el7_4.x86_64
Please see here for updated packages that contain vulnerability fixes https://access.redhat.com/errata/RHSA-2017:2029
You are more than welcome to contact us if you have any follow up questions.
Regards
Elvedin
(CID:134028629)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:48 PM . Last Modified: 2024-04-04 02:46 AM
Hi Elvedin, thanks a lot for your response,
Best regards,
Cees
(CID:134028632)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 10:48 PM . Last Modified: 2023-10-22 04:16 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.
This is a heading
With achievable small steps, users progress and continually feel satisfaction in task accomplishment.
Usetiful Onboarding Checklist remembers the progress of every user, allowing them to take bite-sized journeys and continue where they left.
of
