Issue
Sales literature shows the use of NV202, are these the only supported device and are these provided by Schneider
Product Line
TAC INET, Security Expert
Environment
- Security Expert SP-C
- I/NET Access Control Hardware
Cause
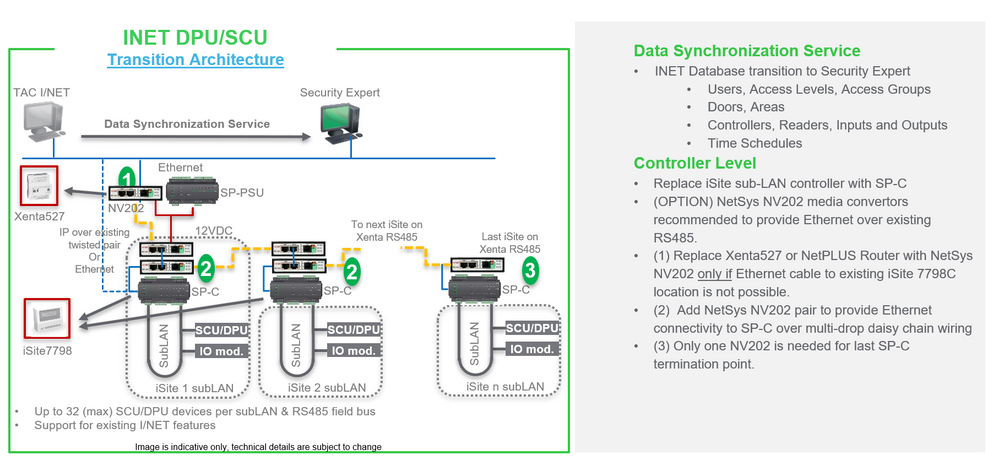
The NetSys NV202 product was sourced to provide a solution for a large I/NET Site that had multiple 7798B / 7798C controllers communicating back to a single Xenta 527. As these I/NET Controller LAN devices only communicate via RS-485, a method of using this existing RS-485 cabling to support the SP-C Ethernet connection needed to be sourced. Tests were carried out to see their performance, which is provided in the resolution below.
These devices are provided by NetSys and if necessary should be purchased directly through their distribution centers. Documentation for this device is also provided on their website.
Resolution
The following shows the tests, methods, and results performed with the NetSys NV-202 on a transition I/NET Database with over 25,000 users and over 5,000 doors.
Testing and Validation of proposed NV-202 based RS485 Network Replacement Solution
Test Equipment
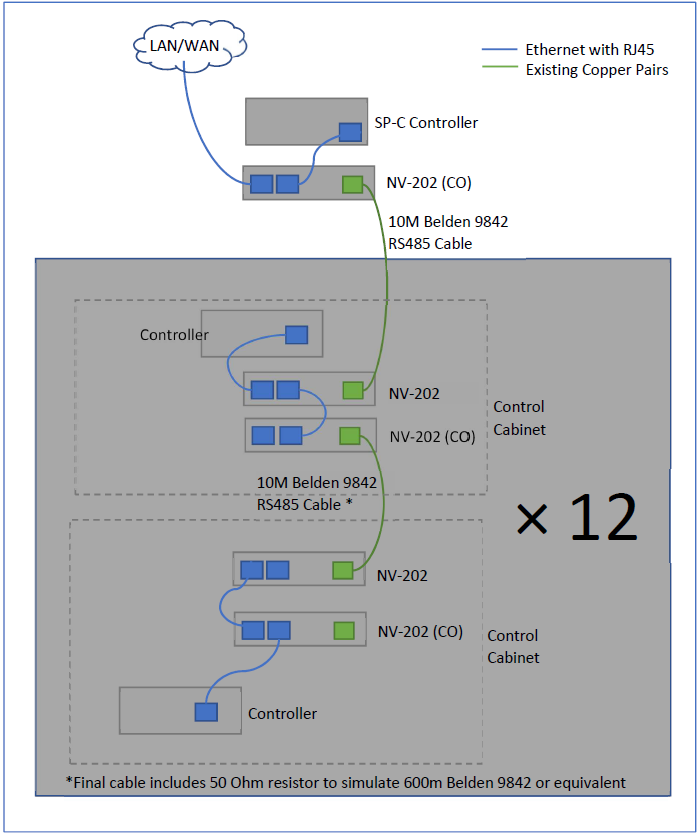
- 49 Netsys NV-202 devices and power supplies
- 25 SP-C Controllers
- Security Expert Software 4.2.251.19 installation on a PC with the following specification:
- Processor Intel(R) Core(TM) i7-3820 CPU @ 3.60GHz
- Installed RAM 16.0 GB
- 240m Belden 9842 Twisted Pair cable PLUS 50 Ohm resistances for line length simulation to an equivalent run length of 840m
- 100Mbps switch for interconnection of server PC and controller LAN
Test Scenario
30 NV-202 units and in the following network topology.
Method
- The Security Expert server was loaded with a database backup from an I/NET Transitioned Site, which was then modified to include:
- Connection to the SP-C’s on the IP range 192.168.1.200-192.168.1.224. by modifying existing real-world controller records to match (Database ID’s 149 onwards)
- Increasing the record load on each controller to the full set of users in the database (21,522) to be downloaded by adding an Access Level containing a door on each controller to each User
- A Status Page containing an All Events window
- All controllers were connected to the same 100Mbps switch as the test PC containing Security Expert
- The last controller in the daisy chain had one input wired into Relay 1 of the controller; this was used to validate input change timing.
- Download was forced to all controllers
- Timing for each required parameter (as noted in Figure 2) was measured using the final controller at the end of the cable run, having worst-case characteristics of bandwidth/latency due to maximum number of daisy-chained NV-202 devices
Figure 2: Tested Timing Parameters
Results
- Command Response Time
Manual commands (by right-clicking and selecting ‘Unlock Door’) were performed on the first door programmed on the SP-C. 25 activations were run and the worst-case results selected.
Command response time is less than 2 seconds as stipulated. See Wireshark capture:Figure 3: Packet capture of a Manual Door Unlock command to the worst-case SP-C from Security Expert Software
- Status Changes Response Time
Relay 1 of the SP-C was activated, which is wired to Input 1 of the same SP-C in order to close the input and trigger a status change. 25 activations were run and the worst-case results selected.
Status Change response is less than 1 second stipulated. - Door Status Changes response time
Manual commands (by right-clicking and selecting ‘Unlock Door’) were performed on the first door programmed on the SP-C. 25 activations were run and the worst-case results selected.
Door status change response is less than 1 second stipulated. - Retrieve access data or user’s data
Not applicable. This data is stored in the server database. - Generate any single ad-hoc reports
Not applicable, reports are generated by the server using data from the server database. - Multiple access control levels
Not Applicable to this test - Security Expert can store unlimited Access Levels, and associate any of them to a given User. Access Level/User quantity limitations are not affected by the NV-202. - EOD download time:
A Force Download operation was performed on the SP-C, and the time to completion recorded. 25 activations were run and the worst-case results selected.
Maximum download time: 58 seconds per controller (noting 21,522 Users) - Time synchronization – maintain synchronism
Time update packets are successfully sent, Server and controller time maintained within 1 second. - Time synchronization – accuracy
Not Applicable to this test – time is updated periodically (not constantly) so not significantly affected by bandwidth or latency.