Ask our Experts
Didn't find what you are looking for? Ask our experts!
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
Search in
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
There have been a lot of discussions here about the default SNMPv1 community string but didn't find anything related to DCO Disaster recovery node (High Availability). The problem is that our security scanners are reporting a vulnerability since the DR seems to be using the default "public" even though we have disabled the SNMPv1 and in addition changed it from "public" to something else.
It seems that these configurations are not taken into use if the DR is not promoted to master? Scans were fine when the DR was the master but once dropped to being a DR, the same vulnerability was found.
(CID:144313595)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
Hi Michael,
SNMP v1 can be disabled both on the master node and the DR node, if haven't tried it yet, please go to server (both master and DR) webmin interface, StruxureWare DC Operation > Setup , un-check the v1 option for "Enable SNMP server", and then push the Setup button:
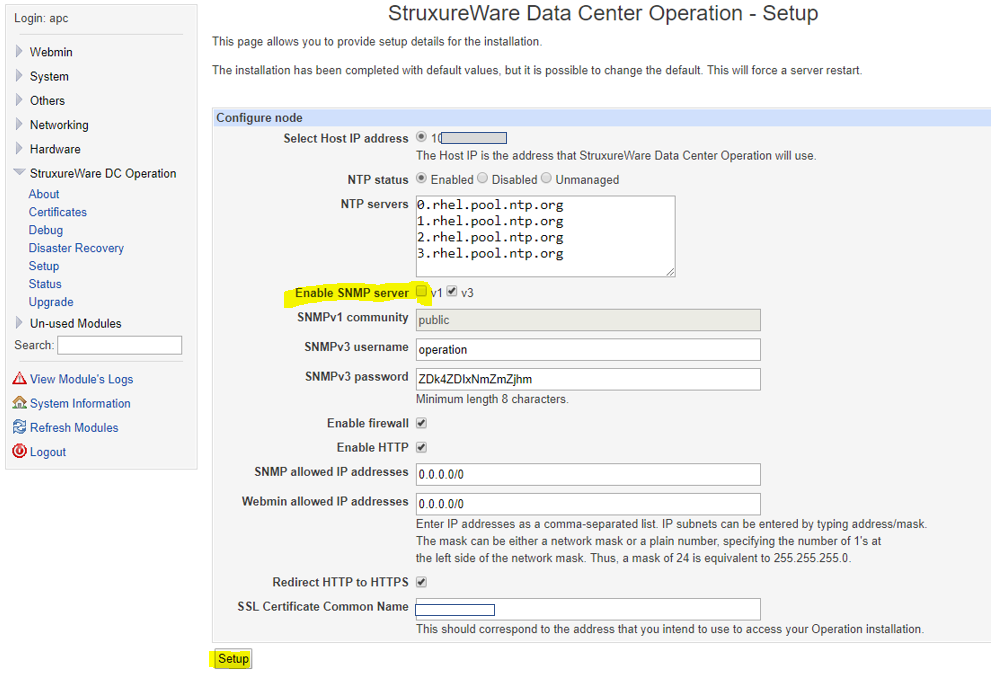
And then check your vulnerability scans to See if that helps, otherwise it would be great if I could have details about your scanning tool and its DCO related reports, thanks.
Kind regards
(CID:144313614)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
Hi Jef!
The SNMPv1 is disabled on both servers. Before disabling, we also changed the community from "public" to something else. Master node passes the scans with no problems, so does the DR if it's promoted to master. But when it is in "standby" as a DR, the scans report: "Default or Guessable SNMP community names: public". So it seems it uses some default values when working as a DR. I'll ask some more information from our IT Security.
(CID:144313625)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
Hi Michael,
Thanks for the info - I will send you an invite to my =S= box shortly so the data safely can be shared with me, thanks.
Kind regards
(CID:144313664)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
Hi Michael,
What is the version of your DCO servers?
Kind regards
(CID:144313851)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
Currently on 8.2.2.
(CID:144313859)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:48 PM . Last Modified: 2024-04-03 02:31 AM
Hi Michael,
I have had a setup (DCO+DR node) using the latest release version (DCO 8.3) that were running the last few days. This setup were included in our daily security scanning without any SNMP security notifications.
In general, it is recommended to update the product (DCO) to latest release version, which should also contain OS related updates.
Kind regards
(CID:144868637)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-05 07:49 PM . Last Modified: 2023-10-22 03:49 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
You’ve reached the end of your document
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.