Ask our Experts
Didn't find what you are looking for? Ask our experts!
Share Your Feedback – Help Us Improve Search on Community! Please take a few minutes to participate in our Search Feedback Survey. Your insights will help us deliver the results you need faster and more accurately. Click here to take the survey
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
Search in
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:51 PM . Last Modified: 2024-04-08 01:48 AM
Hi all!
I looked for information how it is correct to execute regeneration of self-signed SSL certificate in PowerChute Network Shutdown for Linux in case of, for example, change of hostname or other sensitive information about the server. Unfortunately found only information how to use a certificate, that has been signed by a Trusted CA instead of the self-signed certificate, no more. For example, FA176886 and PowerChute Network Shutdown v4.2 FAQ.
As in practice in my case everything was very simple 😀. For this purpose just it is necessary to stop the PowerChute service on the server, then to delete two old keystore and PowerChute-keystore files and again to start the PowerChute service.
For example in RHEL/CentOS-6.x:
bashMidnightPCNS in RHEL/CentOS-6.x# service PowerChute stop # cd /opt/APC/PowerChute/group1 # rm keystore PowerChute-keystore # service PowerChute startFor examle in RHEL/CentOS-7.x:
bashMidnightPCNS in RHEL/CentOS-7.x# systemctl stop PowerChute # cd /opt/APC/PowerChute/group1 # rm keystore PowerChute-keystore # systemctl start PowerChuteAfter successful start of the PowerChute service new self-signed SSL certificate already with updated information about a host will be again created, as it was required in our case. That's it.
Very thanks for the support.
(CID:111414736)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:51 PM . Last Modified: 2024-04-08 01:48 AM
This question would be better suited on http://forums.apc.com.
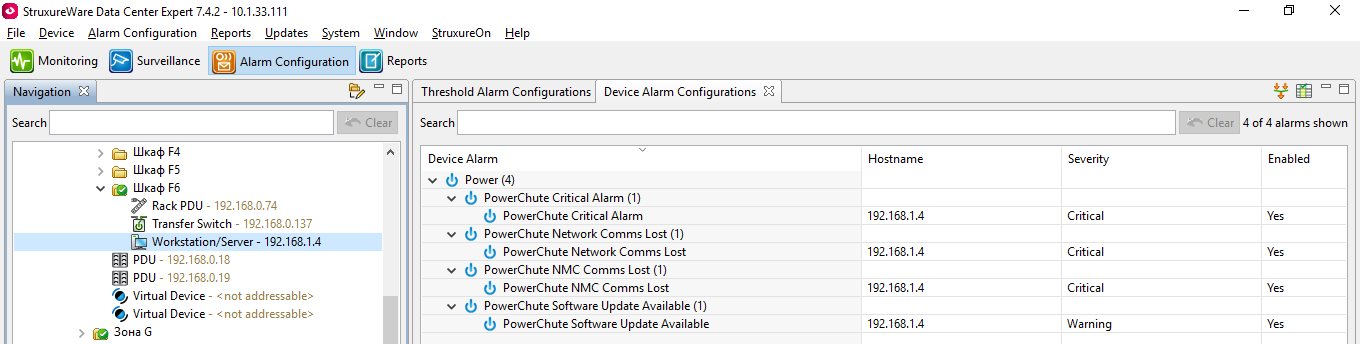
Perhaps, but I think and here for community will interestingly know, that starting with the DCE-7.4.1 is realized support for servers with the installed PCNS-4.2 software (by default in DCE present the appropriate DDF-file). Of course under a condition if PCNS-4.2 was setup with the enabled SNMP. And if it so, then in DCE-7.4.1 and above we see here such "Device Alarm Configurations" for the server with PCNS-4.2:
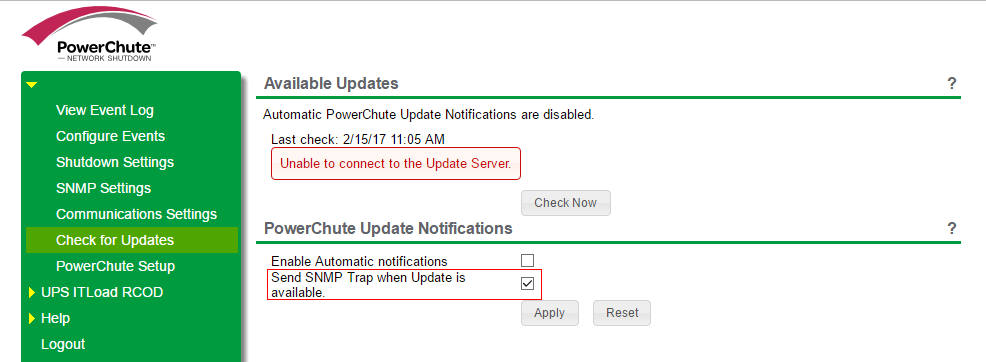
Concerning the Warning "PowerChute Software Update Available": this warning will be active under a condition, if in the PCNS-4.2 settings the "Send SNMP Trap when Update is available" function is enabled:
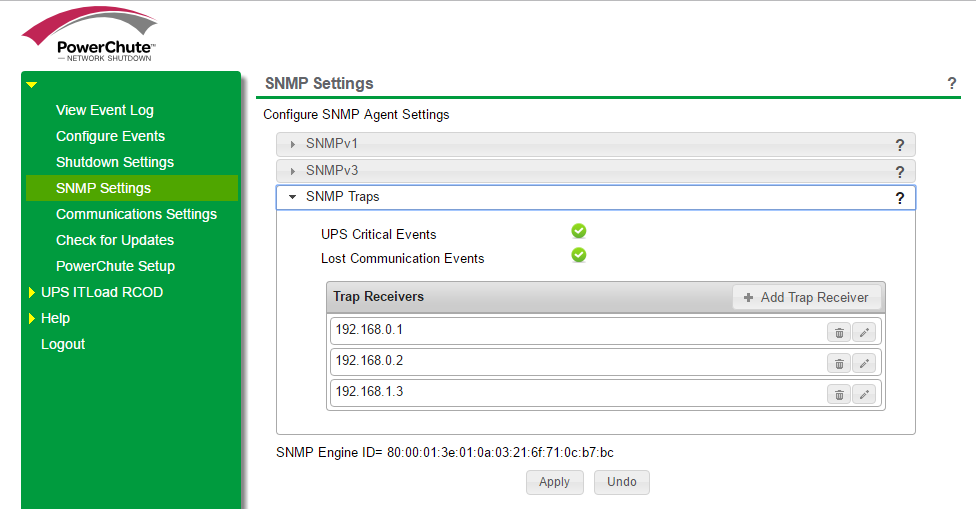
Besides, in the PCNS-4.2 SNMP settings it is necessary to specify as the trap receiver the target server DCE-7.4.1 and above:
P.S.: for successful "Check for Updates" of the PCNS, at the server, where this program is installed there shall be an outgoing access to production update URL: https://updates.apc.com:443/
(CID:111414982)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:51 PM . Last Modified: 2024-04-08 01:48 AM
Spezialist,
This question would be better suited on http://forums.apc.com.
Regards,
Cory
(CID:111414758)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:51 PM . Last Modified: 2024-04-08 01:48 AM
This question would be better suited on http://forums.apc.com.
Perhaps, but I think and here for community will interestingly know, that starting with the DCE-7.4.1 is realized support for servers with the installed PCNS-4.2 software (by default in DCE present the appropriate DDF-file). Of course under a condition if PCNS-4.2 was setup with the enabled SNMP. And if it so, then in DCE-7.4.1 and above we see here such "Device Alarm Configurations" for the server with PCNS-4.2:

Concerning the Warning "PowerChute Software Update Available": this warning will be active under a condition, if in the PCNS-4.2 settings the "Send SNMP Trap when Update is available" function is enabled:

Besides, in the PCNS-4.2 SNMP settings it is necessary to specify as the trap receiver the target server DCE-7.4.1 and above:

P.S.: for successful "Check for Updates" of the PCNS, at the server, where this program is installed there shall be an outgoing access to production update URL: https://updates.apc.com:443/
(CID:111414982)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:52 PM . Last Modified: 2023-10-22 03:37 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
You’ve reached the end of your document
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.