Ask Me About Webinar: Data Center Assets - Modeling, Cooling, and CFD Simulation
Join our 30-minute expert session on July 10, 2025 (9:00 AM & 5:00 PM CET), to explore Digital Twins, cooling simulations, and IT infrastructure modeling. Learn how to boost resiliency and plan power capacity effectively. Register now to secure your spot!
DCE/DCO vulnerable to CVE-2017-1000253 ?
EcoStruxure IT forum
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:07 AM . Last Modified: 2024-04-05 04:41 AM
DCE/DCO vulnerable to CVE-2017-1000253 ?
I read about CVE-2017-1000253. Are we using an affected version of CentOS or any of the other affected LTS Linux distros?
http://www.zdnet.com/article/serious-linux-kernel-security-bug-fixed/
(CID:126158509)
Link copied. Please paste this link to share this article on your social media post.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:07 AM . Last Modified: 2024-04-05 04:41 AM
Hi Cees de Vogel,
On the one hand, according to official information from Red Hat CVE Database we have:
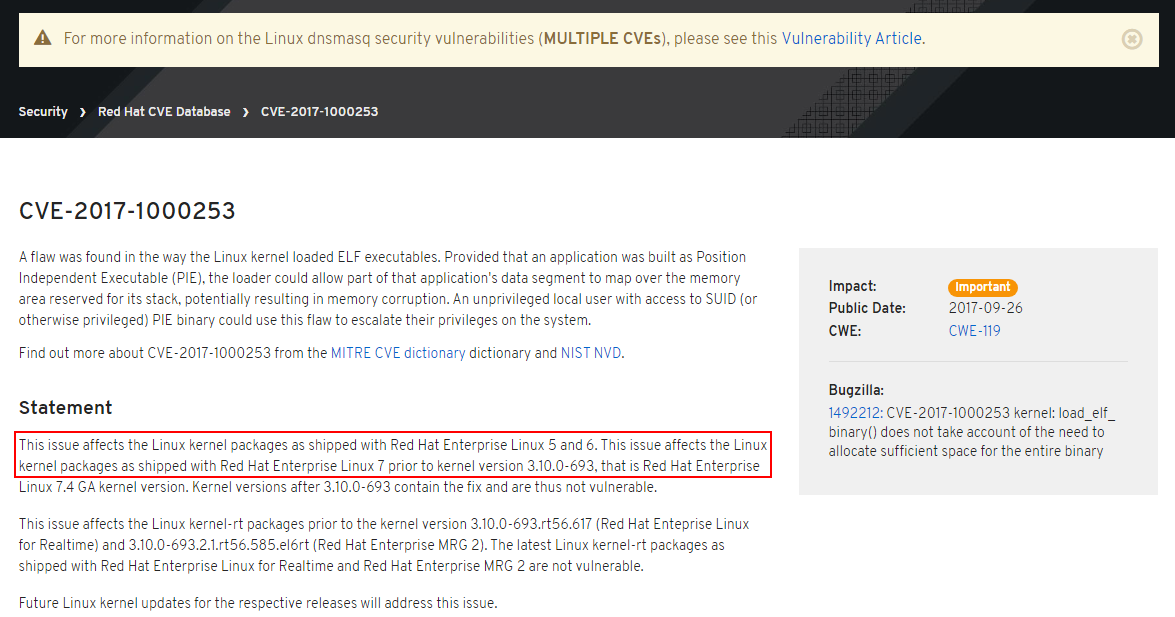
On the other hand, for the latest DCE-7.4.3, according to the information on page Software packages in StruxureWare Data Center Expert, we have:
The StruxureWare Data Center Expert 7.4.0/7.4.1/7.4.3 server OS is CentOS 6.8 (64bit).
kernel 2.6.32-642.4.2.el6
kernel-firmware 2.6.32-642.4.2.el6
Accordingly, the latest DCE software does have the above mentioned vulnerability. And since DCE software is a closed black box, we just have to wait for the new version of DCE software with security fixes...
But with the latest DCO-8.1, everything is much simpler: the installation ISO-image of DCO-8.1 contains CentOS-7.3 and kernel-3.10.0-514.10.2.el7. That is, in this configuration, the latest DCO software also has the above mentioned vulnerability. But this vulnerability can be easily avoided in two ways:
-- Or upgrade the OS of DCO appliance to the current version CentOS-7.4, which was released in early September 2017. You can upgrade it either online (if you have Internet access) or offline (if the DCO appliance is isolated), after downloading the upgrade packages or ISO-image from the official CentOS website. The upgrade process is standard for RHEL/CentOS and can be performed both with the web-GUI webmin and with the Linux console using, for example, the yum command.
-- Or deploy a new server with a fresh installation of CentOS-7.4, and then follow the instructions on page Installing DCO on Red Hat Enterprise Linux 7 to install the latest DCO-8.1 software. This option is preferred for testing the compatibility of the latest DCO software with OS CentOS-7.4. In addition, it is possible to deploy the backup data from DCO software to this new configuration and work with it in the future.
I hope this helps you.
(CID:126158990)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:07 AM . Last Modified: 2024-04-05 04:41 AM
Hi Cees,
On the CVE wensite, that comes up as not found. Can you verify if that is the correct number or not.
Thanks
(CID:126158552)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:07 AM . Last Modified: 2024-04-05 04:41 AM
Hi John,
I just looked at both his links, and the CVE returns a not-found, but, the zdnet article delivers a description of the bug.
I am unsure of the serverity of the bug, as a zdnet user also commented on the article.
Best regards
(CID:126158887)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:07 AM . Last Modified: 2024-04-05 04:41 AM
Hi Cees de Vogel,
On the one hand, according to official information from Red Hat CVE Database we have:

On the other hand, for the latest DCE-7.4.3, according to the information on page Software packages in StruxureWare Data Center Expert, we have:
The StruxureWare Data Center Expert 7.4.0/7.4.1/7.4.3 server OS is CentOS 6.8 (64bit).
kernel 2.6.32-642.4.2.el6
kernel-firmware 2.6.32-642.4.2.el6
Accordingly, the latest DCE software does have the above mentioned vulnerability. And since DCE software is a closed black box, we just have to wait for the new version of DCE software with security fixes...
But with the latest DCO-8.1, everything is much simpler: the installation ISO-image of DCO-8.1 contains CentOS-7.3 and kernel-3.10.0-514.10.2.el7. That is, in this configuration, the latest DCO software also has the above mentioned vulnerability. But this vulnerability can be easily avoided in two ways:
-- Or upgrade the OS of DCO appliance to the current version CentOS-7.4, which was released in early September 2017. You can upgrade it either online (if you have Internet access) or offline (if the DCO appliance is isolated), after downloading the upgrade packages or ISO-image from the official CentOS website. The upgrade process is standard for RHEL/CentOS and can be performed both with the web-GUI webmin and with the Linux console using, for example, the yum command.
-- Or deploy a new server with a fresh installation of CentOS-7.4, and then follow the instructions on page Installing DCO on Red Hat Enterprise Linux 7 to install the latest DCO-8.1 software. This option is preferred for testing the compatibility of the latest DCO software with OS CentOS-7.4. In addition, it is possible to deploy the backup data from DCO software to this new configuration and work with it in the future.
I hope this helps you.
(CID:126158990)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:08 AM . Last Modified: 2024-04-05 04:41 AM
Hi John, Benjamin & Spezialist,
THX for you're reply, yes the first link is broken but when using Google there is enough information to find:
what is the official Schneider answer in this case, is our software affected and if yes when will it be fixed 😀
(CID:126159103)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:08 AM . Last Modified: 2024-04-05 04:41 AM
Hi Cees de Vogel,
In engineering (on DCO) we cannot find this as affecting the product delivered by Schneider. This is as the customer/user has the responsibility for the user access to the server, which they have created at startup. And this attack requires a active user-access to the server, as stated in the first comment on the zdnet article you've linked to.
*This is not a official answer, but, engineerings take on this specific vulnerability.
(CID:126159122)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:08 AM . Last Modified: 2024-04-05 04:41 AM
THX Benjamin
(CID:126159148)
Link copied. Please paste this link to share this article on your social media post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Email to a Friend
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-04 12:08 AM . Last Modified: 2023-10-22 01:15 AM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.
