Ask our Experts
Didn't find what you are looking for? Ask our experts!
Schneider Electric support forum about installation and configuration for DCIM including EcoStruxure IT Expert, IT Advisor, Data Center Expert, and NetBotz
Search in
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:47 AM . Last Modified: 2024-04-09 12:49 AM
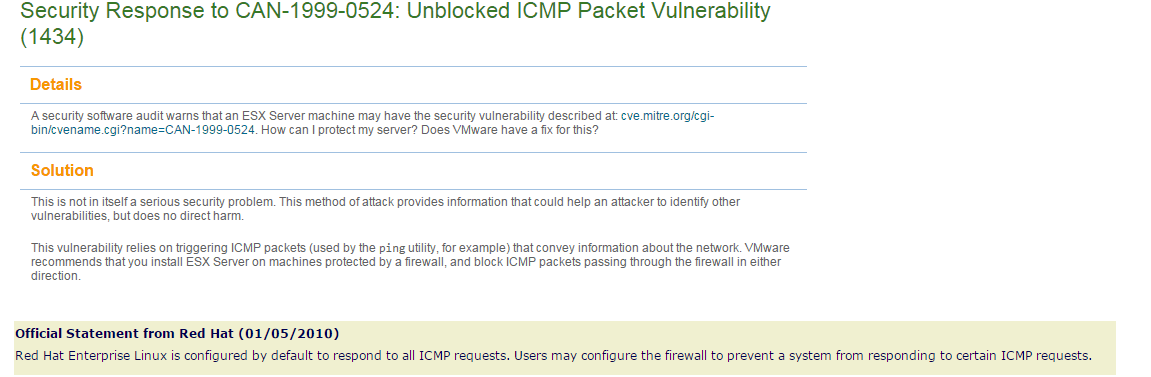
We have picked up that DCE v7.3.1 is vulnerable to CVE-1999-0524. Will there be a patch for this or will be sorted in the next release?
(CID:105467933)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:48 AM . Last Modified: 2024-04-09 12:49 AM
Hi Kevin,
From what engineering has mentioned to me, this CVE in itself does not allow any damage by itselc however as the CVE notes:
ICMP information such as (1) netmask and (2) timestamp is allowed from arbitrary hosts.
If the customer needs to have this information blocked, they can use their router or firewalls to block pings and ping responses. Here was the reply I received:
This CVE pertains to general characteristics of having ICMP enabled on your network or having devices support/respond to ICMP requests. The customer should use their firewall to block these accordingly or they could disable ICMP completely.
Thanks,
Steve
(CID:105467989)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:48 AM . Last Modified: 2024-04-09 12:49 AM
Hi Kevin,
I looked at this vulnerability from 1999 and it is apparently a very low severity.
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-1999-0524
Impact
CVSS Severity (version 2.0):
CVSS v2 Base Score: 0.0 LOW
This vulnerability existed before APC even purchased NetBotz so I'm assuming this was deemed too low to worry about. Still, I will double check with engineering to see if this is something that they can put on their radar but due to the age and severity, I do not think they have been looking at ti nor will they be looking at it going forward.
Just to be sure, what did they use to scan DCE? Do you have the tool's output?
Steve
(CID:105467984)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:48 AM . Last Modified: 2024-04-09 12:49 AM
Thank you Steven.
(CID:105467994)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:48 AM . Last Modified: 2024-04-09 12:49 AM
Hi Kevin,
From what engineering has mentioned to me, this CVE in itself does not allow any damage by itselc however as the CVE notes:
ICMP information such as (1) netmask and (2) timestamp is allowed from arbitrary hosts.
If the customer needs to have this information blocked, they can use their router or firewalls to block pings and ping responses. Here was the reply I received:
This CVE pertains to general characteristics of having ICMP enabled on your network or having devices support/respond to ICMP requests. The customer should use their firewall to block these accordingly or they could disable ICMP completely.

Thanks,
Steve
(CID:105467989)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:48 AM . Last Modified: 2024-04-09 12:49 AM
Thank you Steven. Much appreciated
(CID:105467995)
Link copied. Please paste this link to share this article on your social media post.
Link copied. Please paste this link to share this article on your social media post.
Posted: 2020-07-03 12:48 AM . Last Modified: 2023-10-31 10:25 PM

This question is closed for comments. You're welcome to start a new topic if you have further comments on this issue.
Link copied. Please paste this link to share this article on your social media post.
You’ve reached the end of your document
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.