Share Your Feedback – Help Us Improve Search on Community! Please take a few minutes to participate in our Search Feedback Survey. Your insights will help us deliver the results you need faster and more accurately. Click here to take the survey
Building a cybersecurity strategy
Digital E-books
Read and download our exclusive e-books & whitepapers.
Search in
Improve your search experience:
- Exact phrase → Use quotes " " (e.g., "error 404")
- Wildcard → Use * for partial words (e.g., build*, *tion)
- AND / OR → Combine keywords (e.g., login AND error, login OR sign‑in)
- Keep it short → Use 2–3 relevant words , not full sentences
- Filters → Narrow results by section (Knowledge Base, Users, Products)
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Email to a Friend
- Printer Friendly Page
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Building a cybersecurity strategy
Originally published on Digital E-books by Omaelk | November 19, 2019 02:24 PM
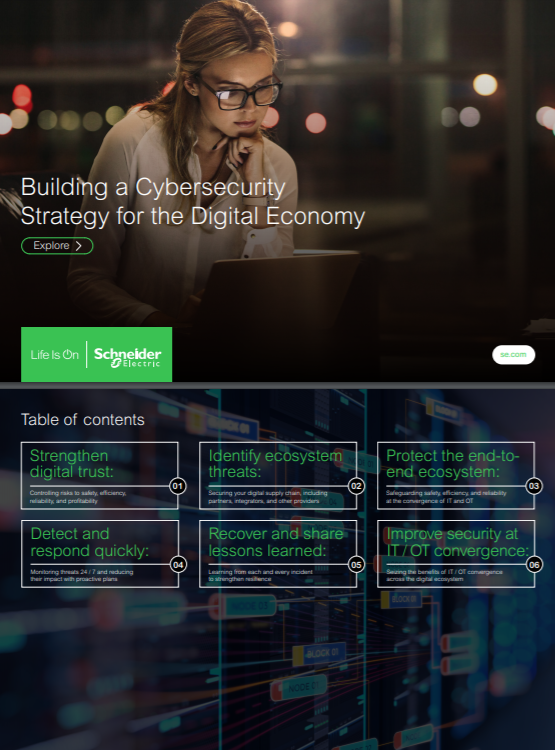
Securing your digital ecosystem
It’s never been more clear: Building and executing a holistic cybersecurity strategy is an urgent business imperative and competitive one, not just a technology issue. But where do you begin?
Discover good practices, with use cases, on ways to:
• Strengthen digital trust
• Identify ecosystem threats
• Protect the end-to-end ecosystem
• Detect and respond quickly
• Recover and share lessons learned
• Improve security at IT/OT convergence
Author
Omaelk
A multi-lingual Global Marketing & Digital Communication/Community Management specialist, mostly involved in Sales enablement & Digital transformation. Born in Morocco, grown up in France, studied in England, worked in the US, I like to consider myself as a world citizen who treasures relationship building, intellectual curiosity & learning agility.
Link copied. Please paste this link to share this article on your social media post.
Would you like to add a comment?
All registered members have full access to the Community and can post comments and start topics.
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.