Manufacturing Cybersecurity: Are Your Industrial Control Systems REALLY Protected?
Industry 4.0 Blog
This blog is addressing the Industry 4.0 and includes news and information aroud topics as smart manufacturing, artificial intelligence and Industrial Internet of Things (IIoT).
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Email to a Friend
- Printer Friendly Page
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Manufacturing Cybersecurity: Are Your Industrial Control Systems REALLY Protected?
Originally published on Industry 4.0 Blog by AUVESY_MDT | October 29, 2019 03:57 PM
Originally written by Gary Gillespie, Vice President of MDT Software for the SE Blog.
Manufacturing is the second most commonly targeted industry by attackers and many attacks are successful due to the many vulnerabilities that exist in Industrial Control Systems (ICS.) ICS encompasses the devices, systems, networks, and controls used to operate and/or automate industrial processes. In many cases, the motivation for the attack is to steal valuable intellectual property, however, a great majority of cybersecurity problems are not caused by malicious attacks but are the result of a negligent or careless employee or contractor. Whether it is an outside or an inside threat, both represent harm to a plant’s operations.
Manufacturers and utility providers are making cybersecurity a greater priority as these attacks can, and often do, result in defective products, production downtime and major safety hazards.
What vulnerabilities exist in manufacturing plants?
Employees/contractors: In 2015, 60% of all attacks were carried out by insiders; employees or anyone who has access to a company’s assets (i.e. contractors.) [1]
Internetworking: New business models related to the Internet of Things (IoT) has made manufacturers more vulnerable as both the industrial and business networks are interconnected to the internet and no longer separated, expanding the attack surface.
The automation layer: One of the easiest and successful ways to launch an attack in a manufacturing facility is to change an automation’s device program data. “While a predefined set of process parameters can be changed through HMI/SCADA applications, the logic maintained on the controller defines the process flow and its safety settings. Therefore, changing the controller logic is both the easiest and most successful way to cause such disruption.” [2]
What technologies exist to secure intellectual property in the automation layer?
There are many products that claim to protect a facility from an attack and while many are useful, none can fully protect control logic from being changed inadvertently or maliciously. The following are the most commonly used cybersecurity products and solutions, along with the risks if manufacturers depend on them alone to protect their Industrial Control Systems.
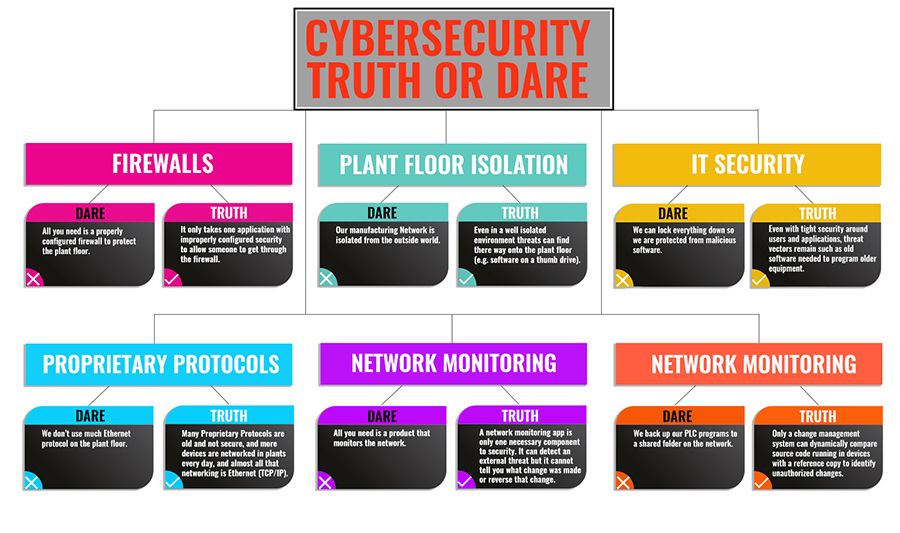
CYBERSECURITY FACTS & MYTHS
Firewalls:
Myth: All you need is a properly configured firewall to protect the plant floor.
Fact: Alone, firewalls have never been enough to completely secure a network. They may intercept many malware attacks, perhaps even the majority, but it only takes one application with improperly configured security to allow someone to get through.
Plant-Floor Isolation
Myth: If the manufacturing network is isolated from the outside world, unauthorized access to the industrial control system is impossible.
Fact: As previously discussed, the combining on the industrial and business networks has increased the vulnerability of the plant-floor to attacks. However, keeping them separated, or providing an “air gap” can also create a false sense of security. Even in a well isolated environment, threats can find their way onto the plant floor. For instance, a USB memory stick with corrupted software can be inserted into a factory-floor workstation. “The Repository of Industrial Security Incidents (RISI) has noted the majority of incidents happen from within the Industrial Control Systems (ICS) network. Other studies note the primary threat as malware being introduced to a system through a USB memory stick.” [3]
IT Security
Myth: Everything can be locked down so the plant is protected from malicious software.
Fact: Even with tight security around users and applications, threat vectors remain, such as having to use old software to program older equipment.
Proprietary Protocols
Myth: If a plant doesn’t use much Ethernet protocol on the plant floor, there is no risk.
Fact: Many Proprietary Protocols are old and not secure. Also, more devices are networked in plants every day and almost all that networking is Ethernet (TCP/IP.)
Network Monitoring
Myth: All that is needed is a product that monitors the network and all PLC programs are backed up to a shared folder on that network.
Fact: A Network Monitoring App is only one component to security. It can detect an external threat but it cannot identify what change was made or reverse that change. Only a Change Management System can dynamically compare source code running in devices with a reference copy to identify unauthorized changes.
What are the best practices?
An integrated approach to cybersecurity is necessary for comprehensive protection and it must include the management of automated device programs and their changes. “Discovering all assets, especially industrial controllers, is critical. This includes maintaining a reliable inventory of configurations, logic, code and firmware versions for each controller.” [2] A sound approach to securing program device data includes three key areas: preparation, detection and recovery.
PREPARE: Secure your program intellectual property
A copy of each program revision needs to be stored in a central repository with a flexible privileging system to manage access.
DETECT: Identify changes made outside the change management system
If the program data on file does not match the program running in the device, the mismatch must be detected, the differences identified and the appropriate people must be notified.
RECOVER: Quickly Undo Unauthorized or Malicious Changes
If a potentially harmful program change has occurred, immediate access to the central repository of all program revisions enables the plant to quickly restore the latest approved program.
Securing your Intellectual Property
Manufacturers can greatly increase their resiliency against a breach to the Industrial Control System simply by knowing right away that a breach has occurred and being able to quickly revert systems back to the state they were in prior to the breach. Per the SANS Institute Survey, Securing Industrial Control Systems – 2017, “Best practices call for programmatic confirmation and improvement of asset documentation, including configuration data, such as control logic with periodic audits backed by change management and automated discovery processes. Tracking at this level allows security personnel to detect breaches or inadvertent, unauthorized changes.”
Stated simply, effective change management of control systems addresses a critical aspect of security not address by data access and network monitoring applications: the Intellectual Property in your device programs.
References:
[1] IBM X-Force® Research “2016 Cyber Security Intelligence Index”
[2] “Cyberthreats Targeting the Factory Floor” IndustryWeek article, Barak Perelman, August 2016
[3] “Spanning the Air Gap: ICS Network Security” Automation World, Larry Asher and Dominic Schmitz, March 2017, Securing your Intellectual Property
Related offers in the Exchange shop:
MDT AutoSave Change Management System
MDT AutoSave Change Management Subscription
- Tags:
- automation change management
- cyber attack
- cyber security
- cybersecurity
- detect malicious changes
- IIoT
- industrial controls
- inustrial control systems
- program backup
- program compare
- program version
- secure program data
- unathorized changes
Author
Link copied. Please paste this link to share this article on your social media post.
Would you like to add a comment?
All registered members have full access to the Community and can post comments and start topics.
Create your free account or log in to subscribe to the board - and gain access to more than 10,000+ support articles along with insights from experts and peers.